The story of mobile phishing through statistics
As organizations take steps to enable mobility in the workforce and the lines between work and personal devices become blurrier, IT administrators must learn how mobile phishing is a looming threat that can affect any organization.
Many end users rely on smartphones and tablets for both entertainment and productivity. In a corporate setting, users rely on email as one of the main channels of communication, but many organizations are moving to other unified communication platforms such as Microsoft Teams and Slack or cloud productivity suites such as Microsoft 365 and Google Workspace. Almost every one of these cloud services has web and mobile applications, making them some of the most common methods users access corporate data via a mobile device.
Due to this increased accessibility to corporate data on mobile devices, they are one of the fastest-growing targets for phishing and other cybersecurity threats. To add to that, SMS and iMessage-based messaging is still a very common mode of mobile communication -- both personal and work-related -- meaning users have consistent access to a phishing vector in their pocket.
The growth of social messaging through applications such as Facebook, Facebook Messenger, TikTok, Instagram and even LinkedIn has expanded the mobile device attack vectors for phishing and security vulnerabilities, so organizations have to meet this challenge with a strong understanding of mobile phishing and the statistics behind it.
Many mobile device users have reported more and more spam messages and calls targeting them over the past few years. Over time end users learned how to spot these fake emails and ignore, delete or report them, but technology and tactics are evolving for victims and perpetrators. Hackers are finding more ways to expose end-user vulnerabilities.
Phishing attacks and attempts come in many different forms. One of the most common vectors is an end user receiving a sketchy text message, usually containing a link to a website. In some cases, clicking the link could expose an end-user device; this was the case when Jeff Bezos' compromised device exposed corporate information after it accessed a malicious file within a WhatsApp message.
The latest iterations of these phishing messages are carefully designed to trick an average user into believing it could be real. This results in more users divulging critical information such as personal and corporate credit cards, account numbers or passwords. This simple concept is the source of numerous vulnerabilities.
While text messaging is one of the most common phishing methods, hackers can expose information via any messaging service or app that is present on an end-user device through the use of links, QR codes and even audio calls or messages.
A highly publicized example of this was a 17-year-old in Florida accused of taking over the Twitter accounts of numerous celebrities, including Elon Musk and Bill Gates, to scam people into sending them Bitcoin. This attack involved the hacker gaining access to specific Twitter employees' credentials that allowed them to carry out this large-scale scam.
According to the Verizon 2021 Data Breach Investigations Report, hackers that use phishing have taken advantage of the confusion with the pandemic and quarantine periods to pump up their frequency of attacks. The same report notes that 36% of recorded breaches are from phishing -- a marked increase from the 25% reported last year.
IT teams use a combination of tools to protect Windows and macOS endpoints, and many of those tools can identify threats from email and web, utilizing web gateways, proxies and firewalls to do so. However, these tools can't treat mobile devices the same way as desktop endpoints as the OS structure and architecture are very different. Similar to a desktop endpoint, mobile devices need that level of security because it allows for access to both the end user and the corporation's data.
Zimperium, a mobile security vendor, reports that more than 85% of organizations have fallen victim to phishing attacks. That same report lists three main attack vectors for mobile devices:
While tools such as firewalls and gateways may help with desktop endpoint protection, those measures aren't as effective for mobile devices. This is because mobile devices are often away from the corporate network, exposing them to many different environments and potential vulnerabilities from unsecured Wi-Fi and device OS patch vulnerabilities. Further, many traditional security platforms for desktop endpoints do not provide the necessary protection against zero-day attacks for mobile devices.
A great example of this is a vulnerability on Apple mobile devices running iOS 14, which mobile security vendor Lookout exposed to the public. Devices running iOS 14.3 or earlier have a flaw in the iOS kernel that may -- in some situations -- allow malicious mobile applications to elevate their privileges on that Apple device. Apple patched this exploit with iOS 14.4, but the flaw could give a hacker complete access to a device that isn't fully updated. That device's lack of update posture could also allow malicious mobile apps to infiltrate your data. This was a serious exploit. While Apple is known for the security of its devices, it shows that no device, iOS, Android or otherwise, is safe from all vulnerabilities.
While phishing is not a new concept and can affect any device, organizations are seeing a trend emerge, with mobile devices becoming a more prominent target. The pandemic has fueled the mobile phishing explosion as users began to work from home and increased mobile device usage to access corporate data.
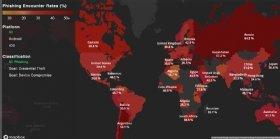
Lookout's Mobile Phishing Map shows that the phishing encounter rate for the U.S. is 34% for both iOS and Android combined.
That rate is even higher outside the U.S., with Russia hitting an encounter rate of 64.5% and Australia at 41.1%. These statistics illustrate two main things.
Some apps that aren't attempting to hack the devices may still collect data on a user, but many organizations will be concerned about this type of tracking and data leakage.
While many desktop security platforms don't do enough for mobile devices, technologies such as mobile device management (MDM) are excellent starting points. These allow IT administrators to secure devices with configurations such as requiring a pin code, enabling encryption and enabling data loss prevention (DLP) on corporate applications. Further, these platforms can disable certain device features and reset devices if they're lost or compromised.
However, MDM platforms do not prevent phishing, man-in-the-middle attacks or zero-day vulnerabilities. To add that additional layer of security, organizations should consider tools such as Mobile Threat Defense (MTD) and Mobile Threat Detection and invest in training and resources to help users identify phishing threats and attempts.








