Medusa malware ramps up Android SMS phishing attacks
The Medusa Android banking Trojan is seeing increased infection rates as it targets more geographic regions to steal online credentials and perform financial fraud.
Today, researchers at ThreatFabric have published a new report detailing the latest tricks employed by the Medusa malware and how it continues to evolve with new features.
Medusa on the rise
Medusa (aka TangleBot) is not a novel banking trojan, but it has seen increased distribution, with campaigns now targeting North America and Europe using the same distribution service as the notorious FluBot malware.
BleepingComputer previously reported that the Medusa and FluBot trojans had previously used 'duckdns.org,' a free dynamic DNS abused as a delivery mechanism, so this is not the first sign of overlap between the two.
In a new report by ThreatFabric, researchers have discovered that MedusaBot is now using the same service as FluBot to perform smishing (SMS phishing) campaigns.
"The samples seen in side-by-side campaigns with Cabassous are identified by the actors themselves with the tags FLUVOICE, FLUFLASH and FLUDHL (possibly as a reference to the corresponding Cabassous/Flubot campaigns)," ThreatFabric explains in their report.
The researchers believe that the Medusa threat actors began using this distribution service after seeing how widely spread and successful FluBot's campaigns had become.
Medusa's main strength lies in its abuse of the Android 'Accessibility' scripting engine, which enables actors to perform various actions as if they were the user.
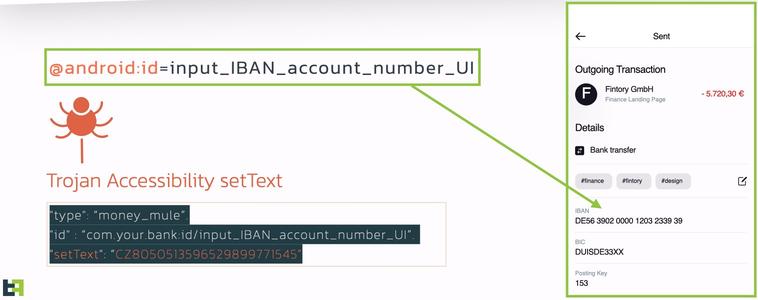
These actions are:
All in all, it’s a highly capable banking trojan with keylogging features, live audio and video streaming, remote command execution options, and more.
ThreatFabric was able to gain access to the malware's backend administration panel and found that its operators can edit any field on any banking app running on the device. This feature allows the malware to target almost any banking platform with fake phishing login forms to steal credentials.
The malware is commonly distributed spoofed DHL or Purolator apps, but the researchers also saw packages masquerading as Android Update, Flash Player, Amazon Locker, and Video Player.
These APKs are manually installed by the victims themselves, who receive an SMS message with a URL leading to a site pushing the malicious Android app.
To prevent being infected by these malware infections, always treat strange URLs sent from your contact list as untrustworthy as they may have been sent by malware on the senders' device.
As always, do not, under any circumstance, download APKs from unknown websites, as they invariably lead to malware infections.
Related Articles:
SharkBot malware hides as Android antivirus in Google Play
TeaBot malware slips back into Google Play Store to target US users
New Xenomorph Android malware targets customers of 56 banks
Roaming Mantis Android malware campaign sets sights on Europe
Android trojan persists on the Google Play Store since January








